|

|
 |
Although achieving host mobility for ![]() native applications is
straight-forward, many legacy applications will remain
native applications is
straight-forward, many legacy applications will remain ![]() /ROAM
unaware. In designing a solution for these applications, our primary
goals are to remain transparent to both applications and the TCP/IP
protocol stack. The main host modification required for legacy
applications is a user-level ROAM proxy. The proxy serves the
following functions: (1) encapsulates and decapsulates IP packets
within
/ROAM
unaware. In designing a solution for these applications, our primary
goals are to remain transparent to both applications and the TCP/IP
protocol stack. The main host modification required for legacy
applications is a user-level ROAM proxy. The proxy serves the
following functions: (1) encapsulates and decapsulates IP packets
within ![]() packets, (2) determines the triggers of remote hosts, and
(3) sends the local private trigger to remote hosts.
Table 1 gives the notations used in this section.
packets, (2) determines the triggers of remote hosts, and
(3) sends the local private trigger to remote hosts.
Table 1 gives the notations used in this section.
 |
We assume that each host ![]() has a current IP address denoted by
has a current IP address denoted by
![]() and a home IP address (e.g., the address of the host in its
home network) denoted by
and a home IP address (e.g., the address of the host in its
home network) denoted by ![]() . The home address is stored in the
end-host's DNS record, and it is used as a source address for all
packets sent by legacy applications on
. The home address is stored in the
end-host's DNS record, and it is used as a source address for all
packets sent by legacy applications on ![]() . Each host
. Each host ![]() runs a
ROAM proxy
runs a
ROAM proxy ![]() that maintains a public trigger
that maintains a public trigger ![]() where
where
![]() is computed as a hash on
is computed as a hash on ![]() 's home IP address, and
's home IP address, and ![]() contains the current address of
contains the current address of ![]() and
and ![]() 's port number, i.e.,
's port number, i.e.,
![]() . The proxy is responsible for updating the trigger
every time the host's current IP address changes.
. The proxy is responsible for updating the trigger
every time the host's current IP address changes.
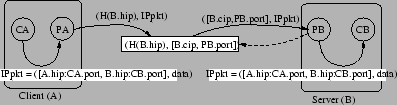
Figure 6 shows a typical data path in a legacy
application, where a client ![]() running on host
running on host ![]() is accessing a
web server
is accessing a
web server ![]() running on host
running on host ![]() .
(Figure 8 shows the pseudo-code executed by
an ROAM proxy.) The source and the destination addresses in the headers
of the packets sent by CA are the host IP addresses of
.
(Figure 8 shows the pseudo-code executed by
an ROAM proxy.) The source and the destination addresses in the headers
of the packets sent by CA are the host IP addresses of ![]() and
and ![]() ,
respectively. Upon capturing the packet,
,
respectively. Upon capturing the packet, ![]() encapsulates it in
encapsulates it in
![]() and proxy headers and sends it to
and proxy headers and sends it to ![]() through
through ![]() using UDP.
6The identifier of the packet is set to
using UDP.
6The identifier of the packet is set to ![]() 's public trigger identifier,
i.e.,
's public trigger identifier,
i.e., ![]() (see function ip_receive in
Figure 8). The format of the packets handled
by
(see function ip_receive in
Figure 8). The format of the packets handled
by ![]() proxies is shown in Figure 7
proxies is shown in Figure 7
When this packet arrives at ![]() (see
(see
![]() ),
), ![]() 's proxy
(
's proxy
(![]() ) strips off the
) strips off the ![]() and proxy headers and forwards the packet to
the local application. In addition,
and proxy headers and forwards the packet to
the local application. In addition, ![]() checks to see if the packet is
addressed to its own public trigger. If it is, then
checks to see if the packet is
addressed to its own public trigger. If it is, then ![]() knows that
knows that ![]() 's
proxy (
's
proxy (![]() ) does not have a private trigger for
) does not have a private trigger for ![]() , so
, so ![]() should
send one. As an optimization,
should
send one. As an optimization, ![]() sets a timeout to see if it can
piggyback the trigger on a packet sent from
sets a timeout to see if it can
piggyback the trigger on a packet sent from ![]() 's application
(
's application
(![]() ). Otherwise, when the timeout expires,
). Otherwise, when the timeout expires, ![]() 's proxy sends the
private trigger in a separate packet. An end-host chooses private triggers
on a per flow or a per communication peer basis. This precludes a malicious
end-host from learning the private trigger used by (the flows of)
another end-host and eavesdropping on it.
's proxy sends the
private trigger in a separate packet. An end-host chooses private triggers
on a per flow or a per communication peer basis. This precludes a malicious
end-host from learning the private trigger used by (the flows of)
another end-host and eavesdropping on it.
Assume that ![]() does send a packet before the timeout expires,
then
does send a packet before the timeout expires,
then ![]() piggybacks
piggybacks ![]() 's local private trigger on the outgoing
packet to
's local private trigger on the outgoing
packet to ![]() . Since,
. Since, ![]() does not know
does not know ![]() 's private trigger,
it uses
's private trigger,
it uses ![]() 's public trigger (as
's public trigger (as ![]() ). When
). When ![]() receives this
packet, it inserts
receives this
packet, it inserts ![]() 's private trigger into its translation table
with
's private trigger into its translation table
with ![]() as the key. In addition,
as the key. In addition, ![]() sees that the packet was
sent to its own public trigger, so it also sets a timeout and tries to
piggyback its private trigger to
sees that the packet was
sent to its own public trigger, so it also sets a timeout and tries to
piggyback its private trigger to ![]() .
.
When ![]() changes its IP address from
changes its IP address from ![]() to
to ![]() as a result
of moving from one subnetwork to another,
as a result
of moving from one subnetwork to another, ![]() will insert a trigger
containing the new IP address
will insert a trigger
containing the new IP address ![]() into
into ![]() and remove
the trigger containing the old IP address
and remove
the trigger containing the old IP address ![]() . The trigger
identifier itself remains the same. Effectively, host mobility is
masked by the
. The trigger
identifier itself remains the same. Effectively, host mobility is
masked by the ![]() network from the communicating peer, and end-to-end
connectivity is preserved.
network from the communicating peer, and end-to-end
connectivity is preserved.
While each end-host initially chooses its private triggers such that they are stored on nearby servers, end-hosts may eventually move far from those servers. To address this problem, each end-host can re-sample trigger servers either periodically or once it notices that its current private triggers are experiencing a high latency. The new private triggers can be exchanged using a mechanism identical to the one used to exchange the original private triggers via the public triggers. The only change occurs in the i3_receive function: in addition to comparing the packet identifier to the the host's public trigger, we also compare it to the previous private trigger identifier, and then send out the new private trigger if necessary. This operation will be transparent to applications.