- ... Shenker1
- ICSI Center for Internet Research (ICIR), Berkeley, shenker@icsi.berkeley.edu
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... identifier2
- In the implementation presented in this
paper, we use
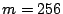 . Such a large value of
. Such a large value of 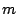 allows end hosts
to choose trigger identifiers independently since the chance of
collision is minimal. In addition, a large
allows end hosts
to choose trigger identifiers independently since the chance of
collision is minimal. In addition, a large 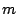 makes it very hard for
an attacker to guess a particular trigger identifier.
makes it very hard for
an attacker to guess a particular trigger identifier.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... refreshed.3
- To make
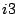 server failure
completely transparent to end-hosts,
server failure
completely transparent to end-hosts, 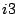 can replicate
triggers [6].
can replicate
triggers [6].
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... server4
- Since
the trigger can be reused across connections, the
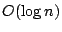 traversal only needs to be done when
traversal only needs to be done when 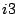 servers fail or when using a
trigger for the first time.
servers fail or when using a
trigger for the first time.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...
5
- Note this is a generalized form of triggers, which
allows a trigger to send a packet to another identifier
rather than to an address.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... UDP.6
- In order to avoid fragmentation due to the
encapsulation, the maximum segment size (MSS) TCP header option
in a SYN packet is decremented accordingly.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... TUN7
- The TUN
virtual interface is implemented by the Universal TUN/TAP driver,
which is included as a standard feature of the kernel in Linux 2.4 and
later.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... servers.8
- There is little
performance improvement for more than
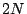 servers because at that
point, each domain is likely to have a server.
servers because at that
point, each domain is likely to have a server.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... stretch9
- Calculated as the ratio of the path latency using a
particular mobility scheme to the shortest path latency on
the underlying network topology.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... Infrastructure.10
- Another
possibility would be to use DNS to store public keys, but then ROAM
would be as secure as the DNS.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
