
Next: Implementation Methodology and Testbed
Up: Architecture Design
Previous: Filter Specification
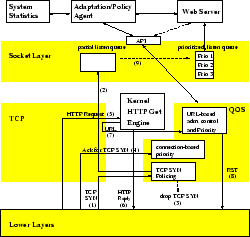
We have developed architectural enhancements for Unix-based servers to
provide these mechanisms. Figure 4 shows the basic
components of the enhanced protocol stack architecture, with the new
capabilities utilized either by user-space agents or applications
themselves. This architecture permits control over an application's
inbound network traffic via policy-based traffic
management [10];
an adaptation/policy agent installs policies into the kernel via a special
API. The policy agent interacts with the kernel via an
enhanced socket interface by sending (receiving) messages to (from)
special control sockets.
The policies
specify filters to select the traffic to be controlled, and actions to perform
on the selected traffic. The figure shows the flow of an incoming request through the
various control mechanisms.
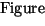 4:
Enhanced protocol stack architecture.
4:
Enhanced protocol stack architecture.
 |
Renu Tewari
2001-05-01

