



Next: The transformation AddRoundKey
Up: On the implementation of
Previous: The required modular arithmetic
Description of the Advanced Encryption Standard
In this section we briefly describe the Advanced
Encryption Standard (AES). For a more detailed description we refer to [DR2].
AES encrypts plaintexts consisting of
lb bytes, where
lb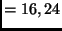 ,
or
,
or 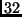 . The plaintext is organized as a
. The plaintext is organized as a
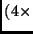 Nb
Nb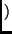 array
array
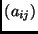 ,
,
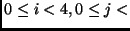 Nb
Nb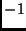 , where
Nb
, where
Nb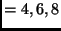 , depending on
the value of
lb. The
, depending on
the value of
lb. The 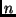 -th byte of the plaintext is stored in
byte
-th byte of the plaintext is stored in
byte 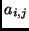 with
with 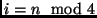 ,
,
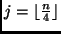 .
AES uses a secret key, called cipher key, consisting of
lk
bytes, where
lk
.
AES uses a secret key, called cipher key, consisting of
lk
bytes, where
lk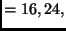 or
or 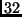 . Any combination of values
lb and
lk is allowed. The cipher key is organized in a
. Any combination of values
lb and
lk is allowed. The cipher key is organized in a
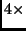 Nk
array
Nk
array 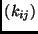 ,
,
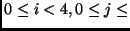 Nk
Nk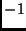 , where
Nk
, where
Nk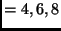 ,
depending on the value of
lk. The
,
depending on the value of
lk. The 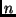 -th key byte is stored in
byte
-th key byte is stored in
byte 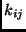 with
with 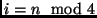 ,
,
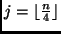 .
The AES encryption process is composed of rounds. Except for the last round, each round
consists of four
transformations called
ByteSub
.
The AES encryption process is composed of rounds. Except for the last round, each round
consists of four
transformations called
ByteSub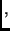 ShiftRow
ShiftRow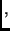 MixColumn, and
AddRoundKey. In the last round
the transformation
MixColumn is omitted. The four transformations operate
on intermediate results, called states. A state is a
MixColumn, and
AddRoundKey. In the last round
the transformation
MixColumn is omitted. The four transformations operate
on intermediate results, called states. A state is a
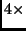 Nb array
Nb array 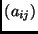 of bytes. Initially, the state is given by the
plaintext to be encrypted. The number of rounds
Nr is
of bytes. Initially, the state is given by the
plaintext to be encrypted. The number of rounds
Nr is 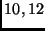 , or
, or
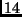 , depending on
, depending on
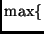 Nb
Nb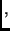 Nk
Nk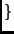 . In addition
to the transformations performed in the
Nr rounds there is an
AddRoundKey applied to the plaintext prior to the first round. We call
this the initial AddRoundKey.
Next, we are going to describe the transformations used in the AES
encryption process. We begin with
AddRoundKey.
. In addition
to the transformations performed in the
Nr rounds there is an
AddRoundKey applied to the plaintext prior to the first round. We call
this the initial AddRoundKey.
Next, we are going to describe the transformations used in the AES
encryption process. We begin with
AddRoundKey.
Subsections



Next: The transformation AddRoundKey
Up: On the implementation of
Previous: The required modular arithmetic
Roger Fischlin
2002-09-25
