 |
 |

However, some on-site hardware maintenance may be needed. Typical issues to be considered are taking care of the fans in the power supply and coping with hardware failures such as hard disk problems. Furthermore, some hardware maintenance on the antennas is needed. Regular inspections of the state of the antennas and mounting hardware are required to ensure safe and reliable operation. Local building safety regulations may also require regular on-site inspections of the set-up.
The Network node can be connected to the users' (home) network in order to give the local user wired access to it. Therefore, on the Ethernet port DHCP is enabled.
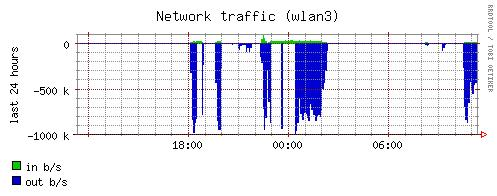
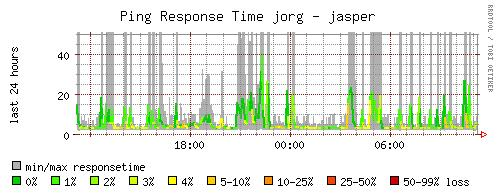
Traffic and other operational data on the node is gathered using RRDB and RRDtool [RRDB] and sent to the central repository at regular intervals. Some examples of graphs used can be found in figure 6.
For simple ``health'' management of the nodes the free version of Big Brother [BB] is used. Big Brother generates a number of ``status lamps'' on the network map available on the website. The combination of the graphs created by RRDtool together with the ok-notok information from Big Brother has shown to be a valuable tool to monitor the network. If the network and its traffic grows, other tools may be needed.