 |

The effect of these changes is that local area networks (LANs) may be bridged over a public network. All that is necessary is that each LAN contain an IPsec bridge connecting it to one or more other LANs. From the point of view of the bridge, the IPsec link is identical to an ethernet network, allowing for creation of arbitrary topologies. Layer-2 and Layer-3 filtering, spanning tree algorithms, etc. may all be used in the IPsec-bridged network with literally no changes.
The modifications needed to the enc and bridge interface code were minimal. For the bridge, the only changes necessary were to allow non-ethernet interfaces to be attached and initialized properly (for example, it is not necessary to switch an enc interface into promiscuous mode). In the enc code, the routine that handles transmission was augmented to pass all enqueued ethernet frames to IPsec for processing and further transmission, after encapsulating them in IP or IPv6. Note that no SPD lookup is necessary here, since the output SA to use is already known.
To support multiple bridge topologies on the same host, a configurable number of enc interfaces is created. This number may be set at kernel compile time. By convention, packets received on SAs that do not have an enc interface associated with them, are made to appear as if they arrived on the enc0 interface. Furthermore, the enc0 interface is not allowed to have any SAs associated with it, nor can it be attached to a bridge. Thus, packets on SAs that have an enc interface associated may be traced or filtered using that interface. For all other SAs, the enc0 interface may be used.
Implementation of the Ethernet-over-IP protocol also proved straightforward, as the output side of the protocol and the first half its input processing are identical to IP-in-IP encapsulation. At the end of input processing, if its input interface is linked to a bridge, the packet is passed to the bridge input routine. If a frame is received over an IPsec SA, its input interface will be the enc interface associated with the SA (see Figures 1 and 2).
In all, less than 300 lines of additional code in IPsec and the bridge were necessary to implemented the virtual LAN functionality.
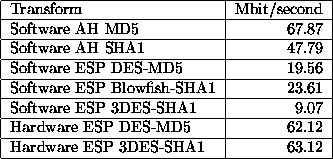
When it comes to performance, the highest cost is, as might be expected, in the encryption. Figure 3 shows the cost of various algorithms (and combinations thereof). Note that AH only performs authentication (the packets are unencrypted).
 |
Note however that it is usually the case that the wide-area network link over which the virtual LAN is established is much slower than the member LANs, and slower than the times shown above. Thus, realistically, the performance is limited mainly by the interconnecting infrastructure. The filtering capabilities of the bridge (blocking multicast/broadcast and non-IP packets) can be of some value here in managing the volume of traffic sent over the encrypted links.
Virtual LAN (vLAN) functionality is offered by a number of bridges, albeit it is used to mean something different from what we have described; more specifically, vLANs are used to compartmentalize a physical network into a number of ``isolated'' LANs. The main goal is to decrease the traffic ``noise'' as seen by machines that do not need to process it (e.g., a printer does not need to receive NFS packets; likewise, normal hosts on the subnet probably do not need to see the AppleTalk packets the printserver uses to submit jobs to the printer). A side effect of vLAN employment is a limited form of security from casual packet sniffing. Such vLANs do not provide the same features our encrypting bridge offers (and vice versa).