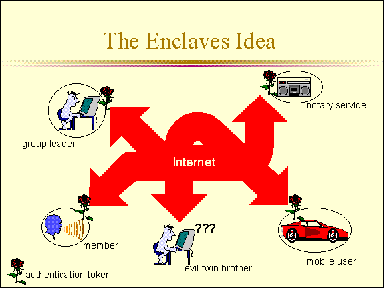
Figure 1: Using Enclaves

Most user interaction and collaboration over the Internet have been primarily via electronic mail. More recently, groupware applications including tele-conferencing have become more widely deployed, especially within large organizations. However, due to the general lack of network security support provided by these systems, groupware has been used mostly within a local-area network environment or over private networks consisting of leased lines.
On the other hand, the openness and lack of security provisions in the Internet have made firewalls a popular instrument for companies and institutions to protect their Internet connections. Such an approach poses two major problems. First, against the widely perceived potentials of the Internet, firewalls make (real-time) user interaction and collaboration much more difficult, if not impossible, especially across organizational boundaries [4]. Second, firewalls cannot be universally applied. For example, small companies or individuals users may not be able to afford the installation and maintenance of firewalls. Moreover, in the case of home users and mobile users, providing an extra, physically separate firewall machine is not practical.
We advocate a method of providing the necessary security while still taking advantage of this broad Internet connectivity through the use of secure ``enclaves,'' where users are protected from outside interference and resistant to security attacks. (Many users ``own'' their desk-top or lap-top machines, so in theory they can turn off unwanted network server daemons on these enclaves.) For example, it would be very desirable for a group of colleagues, who are in different physical locations and are connected through the Internet, to be able to form a secure virtual subnet within which to conduct their joint business. It is also more convenient and economical if the secure formation of these virtual subnets does not depend on firewall machines or extra hardware other than the user machines.
In a fictitious application scenario shown in Figure 1, a group of colleagues are connected via the Internet, where each member is protected by the local enclave (denoted by the ``circle'' around each member). Those in possession of the correct authentication token (the ``rose'') can securely join the group, which is organized by the group leader. One member is using a mobile computer, and another member is a notary service whose job is to take down notes of transactions occured within this session.
In this paper, we describe the design and implementation of a toolkit, called ``Enclaves'', which is a concrete demonstration of how to integrate security into user-level group-oriented applications. It shows that it is feasible for multiple users to collaborate closely, efficiently, and securely over the otherwise unsecure Internet. Our design practices should be useful to systems security architects and our toolkit should facilitate future constructions of secure, network-based collaborative applications.
|
Last changed: 1 May 2002 aw |
|