Figure 5: Starting up

To review the overall workings of the demonstration applications built on Enclaves, let us suppose that Peter, Pat, and John are to add the final touches to a joint research paper, but John is traveling and Pat is working from home. Using today's typical technology, they would probably communicate via phone and electronic mail, and one of them would coordinate changes to the manuscript. This is inconvenient.
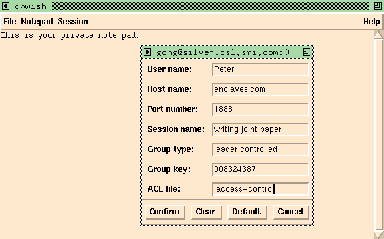
With Enclaves, things are quite different. Peter starts the control panel by typing enclaves at the shell prompt. At this point, Peter can either initiate a new session or join an existing session. Peter chooses to initiate a new session for finalizing the paper. By choosing Start new session from the Session menu, Peter is prompted for a few details, including the name of an access control file (ACL). In this scenario, the ACL file (called .access-control) contains two entries for John and Pat. This process is illustrated in Figure 5.
By clicking the Confirm button, Peter starts a new session and gets a leader window for this session. Choosing the FileSharing menu (see Figure 6), he introduces into the group the file containing the joint paper to be shared among group members. Peter then locks the first few lines of the paper and starts refining the sentences. The locked region is automatically highlighted by a blue foreground and a white background.
A few moments later, Pat chooses to join the existing session. After giving the correct name and password, Pat is admitted to the group and gets a member window, which is similar to that of a group leader, except that it does not have leader functions such as access control. As Pat joins, a message is automatically posted on the group message board notifying this membership change. Figure 6 shows Peter's display at this point.
Pat can see from the shared-file list (under the FileSharing menu) that the joint paper is already inside the group and thus opens it. Immediately, he sees that Peter has locked the first few lines and is working on them. He can instantly observe the changes as Peter makes them. Pat then locks the next paragraph and starts polishing.
Soon afterward, John also joins from the other end of the country via a local modem dial-up and then an Internet connection. The three of them communicate via the message board, working on the sections they choose. Figure 7 is a snapshot of Pat's editor window.
The top region is heavily shaded to indicate that it is currently locked by someone else (Peter, in this case). Similarly, the bottom region is locked by John. The region locked by Pat is the middle section with a solid white background. The rest of the paper - the gray regions - is currently unclaimed. (The locked and unlocked regions are color coded and will be more pleasant to see on a color display.) Each member can modify only a region locked by himself or herself and the group leader mediates the lock-granting process so that no two regions can overlap. These controls ensure that the replicated file copies maintain consistency.
When the completed paper is saved on disk and sent to printers, the group is simply dispersed. Throughout this session, all crucial communications over the Internet are encrypted. These communications include the authentication tokens and messages (passwords are never sent in the clear), messages posted on the group board, the text file, and any changes to it. An outsider cannot join the group for lack of a valid password, and cannot eavesdrop on useful information because of encryption. (We do not consider covert channels or traffic analysis.)
|
Last changed: 1 May 2002 aw |
|