
Next: Results
Up: Approach
Previous: Steps 6 and 7:
Verification of complete authorization is basically carried out in the
same way as complete mediation, with slight modification to the
lattice structure based on the authorization requirement information.
Rather than having a generic checked type qualifier for all
security checks, we assign a type qualifier for each unique security
check. A controlled operation that requires multiple security checks
will then have a type qualifier that is a subclass of the
corresponding type qualifiers of the checks required. For instance,
if a system contains two security checks, denoted by 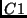 and
and 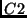 respectively, assuming that the controlling function
respectively, assuming that the controlling function f(file)
requires both security checks to be performed on the file
object, then the type qualifier lattice should be:
partial order {
$checkedForC1C2 < $checkedForC1
$checkedForC1C2 < $checkedForC2
$checkedForC1 < $unchecked
$checkedForC2 < $unchecked
}
Figure 6:
A four-node type qualifier lattice.
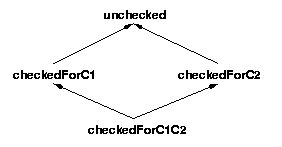 |
Figure 6 shows the graphic representation of the
lattice. Function f should expect the parameter to be of type
checkedForC1C2.
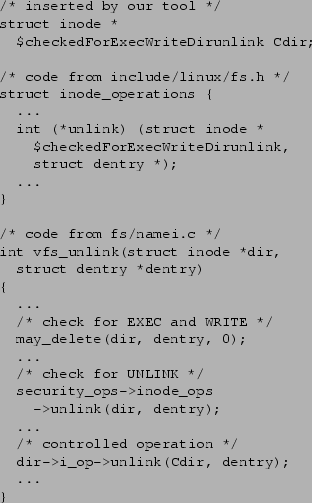
Figure 7 gives an example of a controlled operation
requiring multiple authorizations identified by the runtime analysis
tool [6]. Three security checks are necessary for the
controlled operation unlink() on a directory inode, namely,
permission to traverse the inode, permission to write the inode, and
permission to unlink file in the directory. In the function prototype
definition of unlink(), we specify the authorization
requirement checkedforExecWriteDirunlink. After the security
checks, a new variable Cdir that possesses the right
authorization requirements replaces the old variable dir, and
is passed to the controlling function.
Figure 7:
An example of controlled operation requiring multiple authorizations.
Note that error checking code is removed to make the code easier to follow.
 |


Next: Results
Up: Approach
Previous: Steps 6 and 7:
Catherine Zhang
2002-05-13


