



Next: setuid
Up: The reference functions
Previous: The reference functions
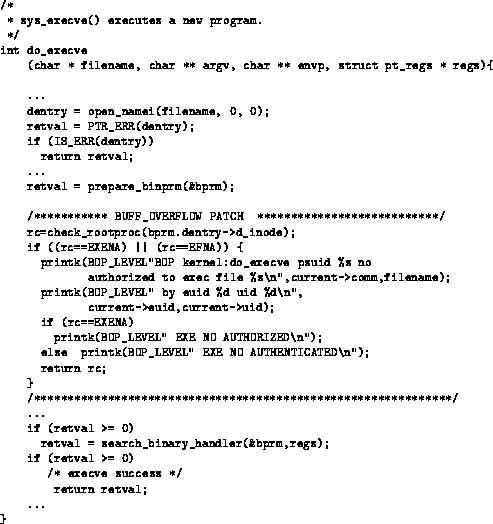
As shown in Figure 3, the new fragment of
code is added at the beginning of this system call right after the
file has been opened. The check_rootproc() function
authenticates the privileged process that invokes the execve
system call and checks in the Access Control Database whether the
calling process has the right to execute the program whose name is
passed as first parameter. The system call execution is denied when
check_rootproc returns one of the two following values:
Figure 3:
The ``patch'' to the execve system call
 |
- EXENA:
- the calling process is not authorized to execute
the requested program. That is, the program name is not present at all in the
Access Control Database or the calling program is not listed in the
programs field of the admitted list in the Access Control Database.
- EFNA:
- the calling process is authorized to execute
the requested program, but the file is not authenticated, e.g. the
modification time or the size do not match.
In the appendix we show the details of the check_rootproc function. If
the calling process does not run with root privileges (EUID=0) then no
further check is performed and the execve proceeds
normally. Otherwise, the service is provided if and only if the
permission is explicitly contained in the Access Control Database.



Next: setuid
Up: The reference functions
Previous: The reference functions
2000-08-22

