



Next: The reference functions
Up: Enhancements to the Linux
Previous: System calls analysis
The Access Control Database
The Access Control Database contains a section for each system call
kept under control. For instance, the working prototype maintains a
setuid_acd data structure to check the access to the setuid system call, and an execve_acd data structure to check
the access to the execve system call.
The layout of execve_acd data structure is shown in Figure
1:
Figure 1:
The layout of the execve_acd data structure
 |
The execve_acd is composed by two arrays of eflst_t structures:
- admitted:
- an executable file F has an entry in this
structure if, at least, one privileged program needs to execute F via an
execve. The information stored in the entry is the list of all
privileged programs which may invoke F.
- failure:
- this list keeps a log of the unauthorized attempts
(that is, not explicitly allowed by the admitted data structure) of
invoking execve by any setuid process.
Figure 2:
The layout of the admitted data structure
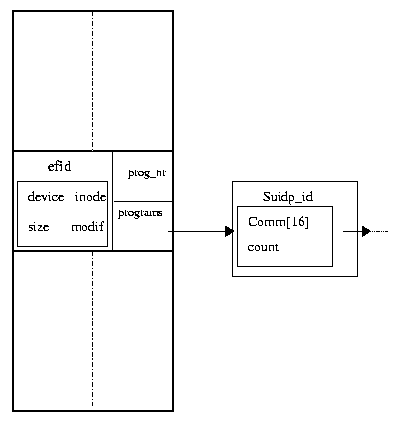 |
Figure 2 shows the admitted data structure which is an
array where each element refers to an executable file and
points to a list of setuid programs that can execute that file.
Each element of the admitted data structure contains these fields:
- efid:
- identifies the executable file F. The
information stored in efid are:
device that is the device number of
the file system to which file F belongs;
inode that is the inode number of file F;
size that is the length in byte of file F;
modif which keeps the last modification time of file F.
The pair of information device and inode identifies file
F in a unique way within the system whereas the information size and modif allow to detect unauthorized modifications of
the file contents.
- programs:
- is a pointer to the list of privileged programs
which can execute file F.
We have introduced a new system call sys_setuid_aclm for reading
and modifying the information kept in the ACD.
This system call can be invoked only by interactive root processes
with EUID=0 and UID=0. These constraints are required to prevent a
subverted setuid or root daemon from tampering the ACD.
The system administrator (root user) can manage the ACD
resorting to the sys_setuid_aclm system call through a
new command, named aclmng which offers the following options:
- -l
- lists the contents of the Access
Control Database kept in kernel space;
- -L
- loads in kernel space the Access
Control Database from file /etc/bop/acd, mostly used during booting;
- -w
- writes the Access Control Database from kernel space into
file /etc/bop/acd, mostly used during system shutdown;
- default
- with no options, -l is assumed.



Next: The reference functions
Up: Enhancements to the Linux
Previous: System calls analysis
2000-08-22

