 |

All keys, certificates and protocol messages used in the implementation of the offline delegation mechanism are specified in a format similar to SDSI [12]. Only the syntax specification of SDSI has been adopted, however, and not its associated public-key infrastructure. We have chosen an external representation that is ``human readable''. That is, the majority of data in the certificate is represented in ASCII. In our experience it is valuable to be able to ``look at'' certificates to compare the fields one by one.
SDSIlib is based on the SEXP library designed and implemented by Ronald Rivest. The library has been extended to support a syntax similar to SDSI and contains sufficient functionality to build parsers and generators for new protocols with SDSI encoding of the protocol messages. The SDSIlib API [5] specifies the external representation of data in SDSI objects, and a set of library functions to manipulate such objects. The library contains basic functions to parse and generate basic SDSI objects. In the SDSIlib port for the Palm-III, most of the library's functionality has been retained. The library can be configured to read and write SDSI objects from and to TCP/IP streams, Unix-like file I/O, or PalmOS databases.
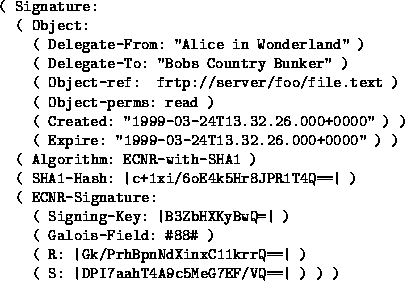
As an example, consider the specification of a Signature object containing a signed delegation statement in Figure 4. The Signature object contains an offline delegation certificate. More specifically, the signed object consists of the information that has been signed (Object), and information (Algorithm) about the signature algorithm that has been used to create the signature in question. The Algorithm field also holds information about the hash algorithm and signature algorithm that have been used to create the digital signature. The format of the Algorithm field is signature-algorithm-with-hash-algorithm. The name of the algorithm-dependent hash field is hash-algorithm-Hash. The name of the algorithm-specific signature field is signature-algorithm-Signature. The fields Object-ref and Object-perms identify the file subject to delegation and the delegated access rights.