



Next: Management and Composition
Up: Detecting and Countering System
Previous: Introduction
This section presents the architecture of ID wrappers. It describes
the capability of ID wrappers naturally provided by the Generic Software
Wrapper Toolkit and our extensions to the toolkit for supporting intrusion
detection.
Figure 1:
Intrusion Detection Wrapper Structure
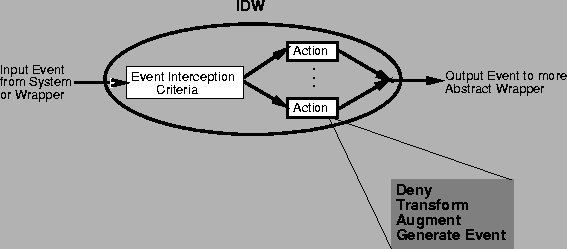 |
Figure 1 gives a high-level view of an ID wrapper. An ID wrapper
is a state machine that is bound dynamically to a program in execution and
that gains control when system calls are invoked.
Multiple ID wrappers may be bound concurrently to a single program in order to
combine multiple ID techniques or to collaborate in the enforcement of a
single policy.
An ID wrapper is specified using the Wrapper Definition Language
(WDL)[10], a superset of C language. WDL supports high-level
specification of the events to be intercepted and accesses to parameters
of the intercepted system call. WDL also hides specific details of different
operating systems so that generic wrappers that run on multiple platforms can
be written. An ID wrapper specified in WDL is compiled by the Wrapper Compiler
(WrapC) into native object code of the destination platform for deployment.
Currently, the wrapper toolkit supports FreeBSD, Solaris, Linux, and
Windows NT1.
ID wrapper capabilities, deriving
from WDL features, fall naturally into two groupings:
- Event Interception Criteria:
- An ID wrapper specifies events that it
intercepts. Such events may be system calls or more ``abstract''
events defined and generated by other wrappers. An ID wrapper will listen to
events that represent steps in attack specifications
[5,9], events defining (or deviating from) behavioral
profiles [3,8], events that attempt to subvert the
intrusion detection system, or events that access system resources
after a successful attack sequence. Events may contain parameters,
and an ID wrapper may condition the interception of the events based on
pre-established groupings (e.g., open, close, read,
write are all ``file'' events), parameter value matching, global
system state, and event sequence relationships (e.g., event e1 that
occur before event e2 will be ``listened for'').
- Actions:
- When an event is intercepted, an ID wrapper may take a variety
of actions. In general, these actions serve to deny, transform, or
augment the event, and perhaps also to generate new events that can be
intercepted by other active wrappers. For intrusion detection and
response purposes, an action will often be to update an intrusion
detection model or fact base, to determine if any misuse rules have
completed or if the current behavior exceeded the defined bounds in the
normal profile, and to take countermeasures if an
intrusion is imminent. Such countermeasures at least will protect the
intrusion detection system from tampering, but also can include a
variety of techniques that prevent damage, deceive the intruder, or collect
additional
information for subsequent legal or military action. At the
implementation level, ID wrapper capabilities derive from WDL facilities that
support convenient access to (and modification of) event parameters,
access to local environment variables and global system state,
generation of new events, and access to lightweight DBMS services.



Next: Management and Composition
Up: Detecting and Countering System
Previous: Introduction
Calvin Ko
2000-06-13

