|

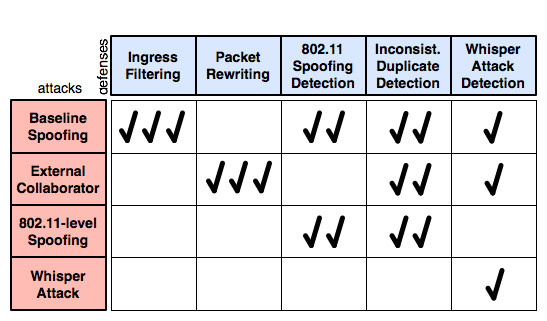
Assuming WPA and VPN solutions comes with a considerable usability cost; we investigate lightweight alternatives. Interestingly, our exploration of defenses against spoofing attacks has revealed a small arms race. In particular, while developing defense techniques we discovered several new variations of the attack, each defeating one of our countermeasures. In this section, we discuss the attacks, the countermeasures and present results evaluating their effectiveness. These findings are summarized in Figure 5. We focus on DNS spoofing for simplicity, but in most cases the attacks and countermeasures are similar for other protocols.