 |

Our integrity Measurement architecture consists of three major components:
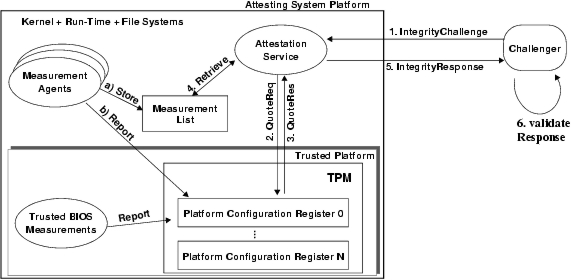
Figure 2 shows how these mechanisms interact to enable remote attestation. Measurements are initiated by so-called measurement agents, which induce a measurement of a file, (a) store the measurement in an ordered list in the kernel, and (b) report the extension of the measurement list to the TPM.
The integrity challenge mechanism allows remote challenger to request the measurement list together with the TPM-signed aggregate of the measurement list (step 1 in Fig 2). Receiving such a challenge, the attesting system first retrieves the signed aggregate from the TPM (steps 2 and 3 in Fig 2) and afterwards the measurement list from the kernel (step 4 in Fig 2). Both are then returned to the attesting party in step 5. Finally, the attesting party can validate the information and reason about the trustworthiness of the attesting system's run-time integrity in step 6.