



Next: Obtaining System State Information
Up: Intrusion Detection Wrappers
Previous: Intrusion Detection Wrappers
ID wrappers need to be properly managed and configured to offer the best
protection to a system.
Depending on the overall ID policy, some ID wrappers should wrap every
process while other ID wrapper should wrap only certain critical processes.
The Wrapper Support Subsystem (WSS) provides support for configuration and
management of ID wrappers. To use an ID wrapper, an administrator first
registers the wrapper with the WSS through a loading process, which
dynamically inserts the run-time image of the wrapper into the kernel.
Selection of processes for wrapping is controlled by activation
(or deactivation) criteria which specify when a loaded
wrapper should begin (or cease) to wrap a process.
The activation criteria language allows specifications based on the invoker,
the program name, and attributes of the executable.
The WSS tracks running processes and evaluates the activate criteria
to activate wrappers to wrap processes that satisfy the criteria.
Therefore, ID wrappers can be configured and administered easily in our
framework to enforce a coherent ID policy.
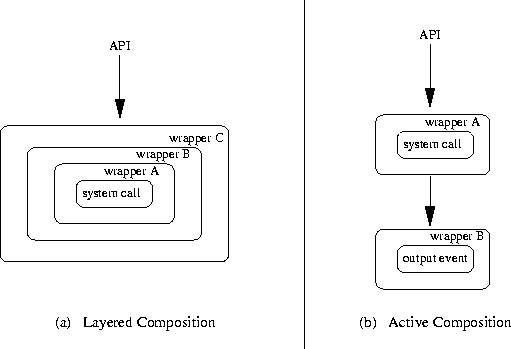
Figure 2:
Wrapper Composition
 |
The whole problem of intrusion detection is beyond the capability of any one
intrusion detection system or ID technique [6].
Therefore, cooperation of different ID techniques is required to
enhance the protection of a system. To combine multiple ID techniques, it
is often convenient to
implement each ID technique in a separate, independent ID wrapper
and to run processes under the simultaneous control of multiple ID wrappers.
Additionally, it is highly desirable to have ID wrappers that are aware
of one another to support hierarchies of increasingly abstract
wrappers. For example, one ID wrapper can listen to system calls to generate
abstract system independent audit events to be consumed by a more abstract
ID wrapper that analyzes the abstract audit events.
Figure 2 shows the two fundamental forms of composition:
- Layered Composition:
- Multiple ID wrappers intercept an event
(e.g., a system call) and perform some actions. In this case, the
actions of the wrappers will be executed in the order in which the wrappers
were installed on the system. Figure 2a
illustrates the ordering for layered composition. In layered
composition, the wrappers involved in the composition might not be
aware of the composition occurring. This type of layering could be
compared to an onion, in which the user's request must travel down
through the ``layers'' of wrappers to get to the system call; the
return value must travel back out through the ``layers'' to reach the
API again.
- Active Composition:
- ID Wrappers generate events intercepted by other
ID wrappers (output events), shown in figure 2b. Output events
represent active composition, in which the wrappers generating the events are
aware of the possible communication/coordination with other wrappers. In this
instance, a ID wrapper generates an output event to be intercepted by
another, usually more abstract, ID wrapper. The more abstract wrapper
will return to the calling wrapper; control passes through the calling
wrapper to the system call.
The two forms of composition are not mutually exclusive: a system event
could be intercepted by layers of ID wrappers, some of which could generate
output events to be intercepted by other ID wrappers.
The composition facility is flexible enough to allows ID wrappers to cooperate
in the manners (e.g., complement or reinforce each other's findings) described
by in Common Intrusion Detection Framework [6].



Next: Obtaining System State Information
Up: Intrusion Detection Wrappers
Previous: Intrusion Detection Wrappers
Calvin Ko
2000-06-13

