Next: Security and Efficiency Considerations.
Up: First Approach
Previous: General Principle.
The most simple solution to manage group key distribution for our
proposal is to share a secret key with each group member and to
encrypt the new group-shared key with each secret key. Each valid
member can decrypt one of the encrypted values to obtain the new
group-shared key.
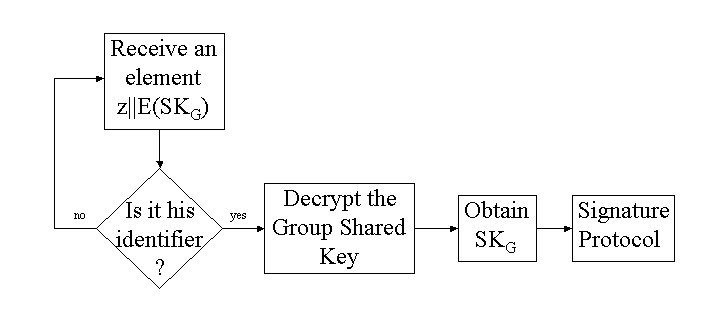
The identifier of the group member can be appended to each
encrypted value. The group member only has to test if it is his
own identifier and to decrypt the corresponding value if it is the
case (see Figure 3).
Figure 3:
First Approach - Getting the Key
|
|
There are some other solutions in the literature that are more
interesting than this simple one. For example, Wong et al.
[16] propose a solution based on a tree, where each leaf
corresponds to a group member and where each node corresponds to a
secret key. Each group member shares with the group manager all
keys that are in the path between their leaf and the root. As
every member knows the key root, this latter is chosen as the
group-shared key. Consequently, for a particular revocation phase,
the GM only has a limited number of values to encrypt, instead of
many in the naive method.
Next: Security and Efficiency Considerations.
Up: First Approach
Previous: General Principle.