 |

Let us reconsider the scenario discussed in Section 2. CMU can deploy AVES to restore bi-directional connectivity within the CMU intranet so that DSL users will be able to access their home computers directly from any host within the CMU intranet. To do so, CMU would deploy waypoints and upgrade its local DNS servers to make them AVES-aware. By upgrading the local DNS servers, initiator-specific bindings can be created easily since an initiator's IP address is now available in the IP headers of its DNS queries to the AVES-aware local DNS servers.
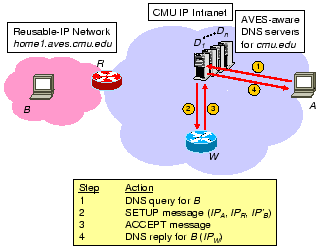
Figure 5 shows how this scheme works. Under this
scheme, reusable-IP networks will use a common domain name suffix, say
aves.cmu.edu, for easy identification. In our example, the
reusable-IP network has a domain name home1.aves.cmu.edu. ![]() -
- ![]() are upgraded AVES-aware local DNS servers. The control path
operations are as follows. Initiator
are upgraded AVES-aware local DNS servers. The control path
operations are as follows. Initiator ![]() 's DNS query for
's DNS query for ![]() is
directly sent to one of the AVES-aware local DNS servers,
is
directly sent to one of the AVES-aware local DNS servers, ![]() (step
1).
(step
1). ![]() is by configuration aware of the IP address of the
AVES-aware NAT gateway
is by configuration aware of the IP address of the
AVES-aware NAT gateway ![]() and the reusable-IP address of
and the reusable-IP address of ![]() . Upon
receiving the DNS query,
. Upon
receiving the DNS query, ![]() selects at random a waypoint among a
set it knows, in this case
selects at random a waypoint among a
set it knows, in this case ![]() , and sends a SETUP message to
, and sends a SETUP message to ![]() (step
2).
(step
2).![[*]](footnote.png) The SETUP message contains
The SETUP message contains ![]() ,
, ![]() ,
and
,
and ![]() , which are necessary to create a data path translation
table entry on
, which are necessary to create a data path translation
table entry on ![]() . When
. When ![]() receives the SETUP message, it examines
its data path translation table to see if it can accept the
request. Let us denote a translation table entry
receives the SETUP message, it examines
its data path translation table to see if it can accept the
request. Let us denote a translation table entry ![]() on
on ![]() more compactly by
more compactly by
![]() . Then,
. Then, ![]() can accept the request for initiator
can accept the request for initiator
![]() , NAT gateway
, NAT gateway ![]() , and responder
, and responder ![]() if and only if,
if and only if,
That is, if ![]() already has a translation table entry for initiator
already has a translation table entry for initiator
![]() , and the responder of that entry is not the same as the one in
the SETUP message, then
, and the responder of that entry is not the same as the one in
the SETUP message, then ![]() must reject the request and reply with a
REJECT message because
must reject the request and reply with a
REJECT message because ![]() cannot be used to relay a particular
initiator to more than one responder. On receiving a REJECT message,
for simplicity, the AVES-aware DNS server will simply do nothing and
let the initiator perform the DNS name lookup again to retry. In our
example, the admission control criterion is satisfied, so
cannot be used to relay a particular
initiator to more than one responder. On receiving a REJECT message,
for simplicity, the AVES-aware DNS server will simply do nothing and
let the initiator perform the DNS name lookup again to retry. In our
example, the admission control criterion is satisfied, so ![]() accepts
the request, creates the corresponding translation table entry, and
sends back an ACCEPT message (step 3). Finally, when
accepts
the request, creates the corresponding translation table entry, and
sends back an ACCEPT message (step 3). Finally, when ![]() receives
the ACCEPT message, it responds to
receives
the ACCEPT message, it responds to ![]() 's DNS query for
's DNS query for ![]() with the IP
address of the selected waypoint,
with the IP
address of the selected waypoint, ![]() , with the time-to-live field
set to zero (step 4). Note that the messages between waypoints and the
AVES-aware DNS servers are authenticated to prevent unknown sources
from gaining control of the system. Also, the messages can be lost in
the network. Waypoint failure and packet loss are simply handled by
initiator
, with the time-to-live field
set to zero (step 4). Note that the messages between waypoints and the
AVES-aware DNS servers are authenticated to prevent unknown sources
from gaining control of the system. Also, the messages can be lost in
the network. Waypoint failure and packet loss are simply handled by
initiator ![]() 's DNS query timeout/retry mechanism. Limitations of this
scheme are discussed in Section 6.
's DNS query timeout/retry mechanism. Limitations of this
scheme are discussed in Section 6.