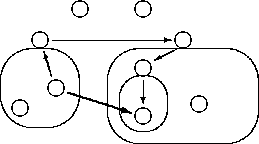
Figure 4: IPC Redirection (``Original'' IPC is denoted by thick lines, redirected IPC by thin lines)

The Lava nucleus provides a general mechanism that can be used for implementing security policies based on IPC redirection. A monitor can be assigned to multiple processes. Any IPC to a process that is administered by another monitor is automatically redirected to this process's monitor which can inspect and handle the message. This can be used as a basis for the implementation of mandatory access control policies or isolation of suspicious processes. For security reasons, redirection must be enforced by the kernel.
A clan is a set of processes (denoted as circles) headed by a monitor. q Inside the clan all messages are transferred freely and

Figure 4: IPC Redirection (``Original'' IPC
is denoted by thick lines, redirected IPC by thin lines)
the kernel guarantees message integrity. But whenever a message tries to cross a clan's borderline, regardless of whether it is outgoing or incoming, it is redirected to the clan's monitor. The monitor may inspect and/or modify the message. Clans may be nested.
Figure 5 shows a monitor which is used to enforce the security policy.
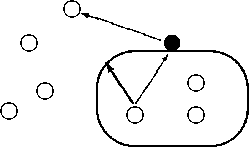
Figure 5: Security-Policy Monitor
All server requests from the encapsulated tasks are inspected by the monitor (filled circle). The monitor drops any request which would violate the security policy. In particular, it uses accounting mechanisms to restrict denial-of-service attacks. Note that all page-faults and mappings are also handled by IPC. Therefore, the according resources are also under the monitor's control.
Instead of enwalling suspicious subjects, monitors can also be used to protect a system from suspicious subjects outside the own clan.
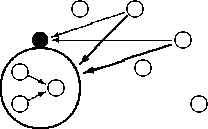
Figure 6: Attack-Blocking Monitor
In figure 6 the monitor (filled circle) inspects all messages coming from the outside and drops messages that cannot be authenticated or do not come from trusted partners. Furthermore, the monitor could encipher sensitive messages automatically (i.e., implement secure channels for its clan members).