 |

All the experiments we run so far were designed to explore specific aspects of the security protocols, under a variety of configurations. In this section we present benchmarks that reflect a more realistic use of these protocols.
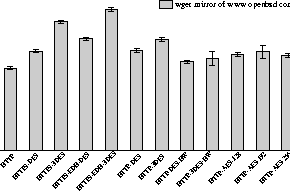
For our first macro-benchmark, we created a local mirror of the www.openbsd.com site, 728 files and a total of 21882048 bytes, to a server machine. We then used wget(1) from a client machine to transfer the whole tree hierarchy over the Intel PRO/1000F network adapters. We used wget(1) instead of curl(1) because of its support for recursive web transfers. Four different ciphers/modes were used for HTTPS. The HTTPS tests used server certificates. The IPsec tests were conducted using manual keying with DES, 3DES, AES and hardware accelerated DES and 3DES. Finally, for completeness, we also included ephemeral Diffie-Hellman results for HTTPS. We present the results in Figure 15.
Our second macro-benchmark is the compilation of the OpenBSD source over NFS (see Figure 16). We present results for 3DES with and without hardware support, as well as AES. As expected, using hardware support for the encryption is particularly useful when the system is burdened with intensive CPU and filesystem loads.