 |

The device must perform the functions of detection, suppression and alert when non-compliant traffic is found to be passing through the network, in a timely manner. Detection refers to determining if a cell being transmitted out of a particular port on a switch is in accordance with the maximum and minimum traffic functions defined for the connection, that is, its VPI/VCI pair. Suppression involves the discarding of the offending cell and Alert refers to a method by which the security device reports the VPI/VCI pair of the offending cell and the switch output which produced it. Optionally, Alert also refers to the reporting of the reason for which the cell is found to be in violation, whether it be due to an illegal VPI/VCI pair or due to a violation of the traffic envelope.
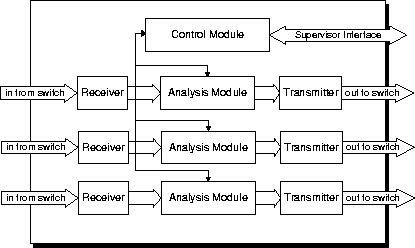
The determining factor in the design was the need to implement the device with components that are widely available, inexpensive, and of proven stability. Because of the high data rates involved in the transmission of cells in ATM networks, it was necessary to use as much parallelism of functions as possible in hardware in order to implement the design with standard components and realizable clock speeds.
Overseeing the operation of the Receivers, Analysis Modules and Transmitters is the Control Module. It is the responsibility of this module to accept data from the Supervisory Interface regarding new connections that need to be admitted in the ATM network and pass this data to the appropriate Analysis Module. Additionally, the Control Module must detect a traffic alert from any one of the Analysis Modules and, when it occurs, must capture the data regarding the cell which caused the alert from the appropriate Analysis Module. Then, the Control Module must transmit this data to the supervisory interface.
The end result is a device that can capture, analyze and retransmit the ATM network traffic on the multiple output ports of an ATM switch, update path information , and report traffic infractions under conditions of peak data rate transmission. The analysis portion of the device's function may be of two types. Under the first variant, arriving network traffic will be checked for validity in terms of whether or not the connection with which that traffic is associated does indeed pass through the network switch and port from which the data originated. The second variant will perform exactly the same verification as the first variant and, in addition, will also verify that traffic that has been found to be traveling across a valid connection has not exceeded the traffic limits placed on that connection.