![[*]](foot_motif.gif) is then used to
encrypt and decrypt data records stored on the PDA, using keys derived
from k.
is then used to
encrypt and decrypt data records stored on the PDA, using keys derived
from k.

Our graphical password schemes are motivated primarily by PDAs that offer graphical input capabilities. We now describe our implementation of a memo pad encryption tool for the Palm Pilot that uses a user-input graphical password to derive the encryption key. The Pilot supports a very natural form of graphical input, and as such, provides an ideal platform for implementing the DAS scheme. Either of the schemes of Sections 2 and 3 could be used to enter the password. Here we illustrate our tool using the DAS scheme.
In our tool, an encryption/decryption key is derived from a DAS
password (i.e., its sequence of coordinates) as follows: Let ![]() be a bit string that represents the sequence of coordinates
(including the unique ``pen up'' indicator). The key k is defined
as
be a bit string that represents the sequence of coordinates
(including the unique ``pen up'' indicator). The key k is defined
as ![]() where h is the cryptographic hash function
SHA-1. This key derivation assures that two distinct coordinate
sequences are transformed (with high probability) into two distinct,
fixed-length keys. Triple-DES
where h is the cryptographic hash function
SHA-1. This key derivation assures that two distinct coordinate
sequences are transformed (with high probability) into two distinct,
fixed-length keys. Triple-DES![[*]](foot_motif.gif) is then used to
encrypt and decrypt data records stored on the PDA, using keys derived
from k.
is then used to
encrypt and decrypt data records stored on the PDA, using keys derived
from k.
Key selection is as follows: the user is prompted with an empty grid to input the password design. Once the password is entered, k is derived and a pre-defined phrase p is encrypted (as Ek(p)) and stored on the PDA. On repeat access, the user is prompted again with the empty grid, upon which she draws the same design. A symmetric key k' is derived and an attempt is made to decrypt Ek(p). If it results in p, then k' = k and the password (and key) is accepted. The user then can proceed to encrypt/decrypt data records. k is deleted from the PDA at the latest when the PDA is powered off.
An adversary who captures the PDA can presumably obtain all of the ciphertext encrypted under k, and since p is either public or stored in plaintext on the device, the adversary has at least one known plaintext/ciphertext pair with which to attack E. For a strong encryption scheme E, however, the best bet for the attacker remains to guess the original password, which, as we will show in Section 3.3, on average is likely to be much harder than if the attacker were faced with attacking a textual password.
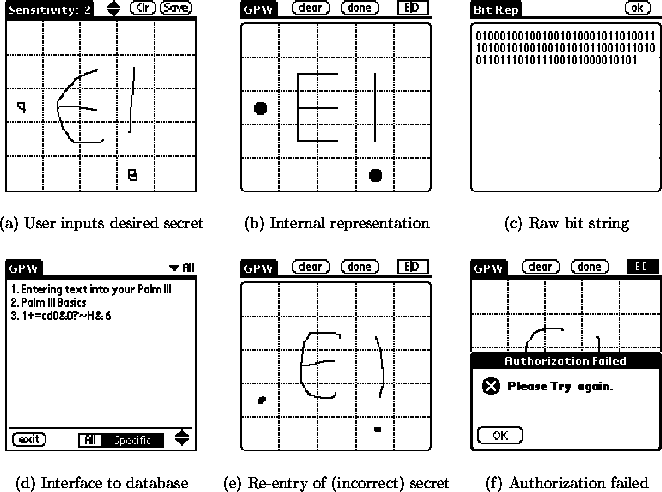 |
The interface for our DAS implementation is shown in Figure 3. Our application shares the database of the memopad application, and allows a user to encrypt/decrypt records in the database based on a user specified drawing. The encryption tool for the Palm Pilot is available from https://cs.nyu.edu/fabian/pilot/gpw.html.