
In this section, we compare Flow Slices with Adaptive NetFlow
[10], a previously proposed solution based on packet
sampling. For the purposes of evaluation, we fix the packet sampling probability
to 1 in 1024 for ANF. To be fair in our comparisons with Flow Slices, we split
the ![]() probability into two parts consisting of packet sampling (
probability into two parts consisting of packet sampling (![]() for our OC-48 trace) and flow slicing probability (
for our OC-48 trace) and flow slicing probability (![]() ). We compare average
error in the estimates for both individual flows (categorized by ranges) as well
as aggregates based on destination port number. typically, are
Table 5 shows that ANF and Flow Slices have similar errors when
estimating the traffic of various applications (aggregated by port). However,
Flow Slices performs better than ANF (by about 10%) in the average error for individual flows. Varying the slice length from 60 to
300 seconds for Flow Slices did not affect the accuracy of the results
significantly, although bigger slice lengths seem to perform a little better
than with smaller slice lengths.
). We compare average
error in the estimates for both individual flows (categorized by ranges) as well
as aggregates based on destination port number. typically, are
Table 5 shows that ANF and Flow Slices have similar errors when
estimating the traffic of various applications (aggregated by port). However,
Flow Slices performs better than ANF (by about 10%) in the average error for individual flows. Varying the slice length from 60 to
300 seconds for Flow Slices did not affect the accuracy of the results
significantly, although bigger slice lengths seem to perform a little better
than with smaller slice lengths.
 |
 |
How does Flow Slices compare with ANF in resource consumption ? Table 6 summarizes the memory usage at the router and the volume of traffic reports for Flow Slices and ANF . Without an inactivity timeout, the resource requirements of the two solutions are similar. As we move to longer bins/slices there is a slight decrease in report volumes and a significant increase in memory requirements. Adding an inactivity timeout of 15 seconds to Flow Slices has a dramatic effect. The memory requirements are reduced significantly (about 80%) at the cost of only a slight increase in the volume of the reports (about 5%). With the inactivity timeout, the memory usage of Flow Slices is less sensitive to the slice length. The lower memory usage of Flow Slices compared to ANF has important consequences when the sampling rates are adapted dynamically. Given the same memory constraints, the sampling rate adaptation algorithm can converge to more aggressive sampling rates for Flow Slices which results in more accurate estimates.
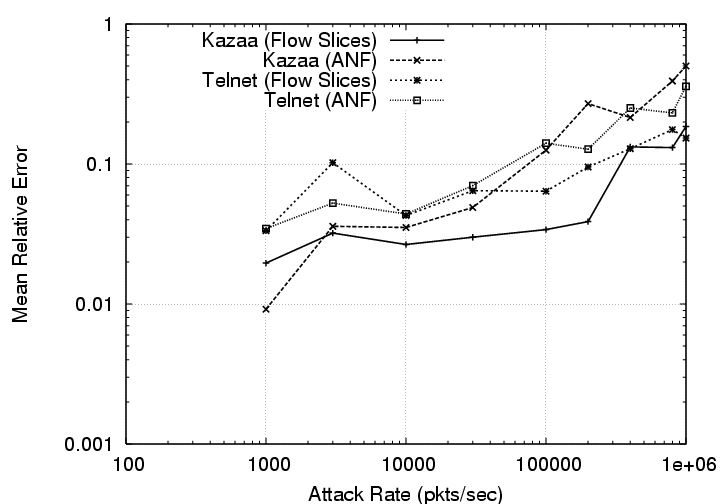
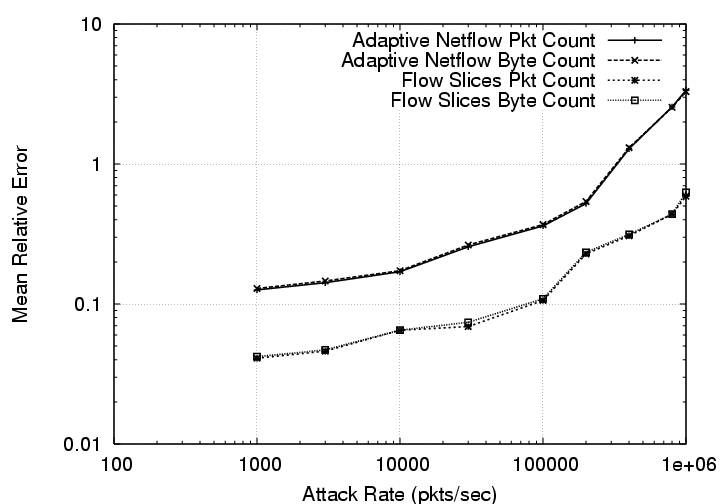
What is the effect of Denial-of-Service attacks? Figure 6.2 compares
the estimates obtained by ANF and Flow Slices in the presence of a DoS attack.
We varied the attack rate from 1000 packets-per-second (pps) to 1.6 million pps;
each attack packet represents a different flow as source addresses are spoofed
at random. We configured ANF and Flow Slices to operate within a memory budget
of 8,000 flow records (not including the buffering needed by ANF to transmit the
records at the end of the measurement bin). ANF converged to smaller sampling
probabilities as attack traffic gained intensity; the sampling probability
varied from 0.155% at 1,000 pps to 0.0026% at 1.6 million pps. Similarly, for
Flow Slices, while the random packet sampling probability remained constant at
![]() (to simulate real hardware constraints), the combined sampling
probability
(to simulate real hardware constraints), the combined sampling
probability ![]() varied from 0.781% to 0.0156%. Flow Slices could afford
more aggressive sampling mainly due to the use of an inactivity timeout of 15
seconds (the slice length for Flow Slices and bin size for ANF were 60 seconds).
On the left, we plot the attack rate on the x-axis and the mean relative error
(both for packet and byte counts) of flows with more than 5,000 packets on the
y-axis, both in log-scale. For comparable memory usage, in the presence of DoS
attacks, Flow Slices produces traffic estimates an order of magnitude better
than those of ANF. On the right, we plot the average relative error in
estimating traffic that belongs to two different applications - telnet and
Kazaa, using the two flow measurement solutions. While the accuracy of both the
estimates reduces as the attack rate increases, Flow Slices provides better
accuracy than ANF.
varied from 0.781% to 0.0156%. Flow Slices could afford
more aggressive sampling mainly due to the use of an inactivity timeout of 15
seconds (the slice length for Flow Slices and bin size for ANF were 60 seconds).
On the left, we plot the attack rate on the x-axis and the mean relative error
(both for packet and byte counts) of flows with more than 5,000 packets on the
y-axis, both in log-scale. For comparable memory usage, in the presence of DoS
attacks, Flow Slices produces traffic estimates an order of magnitude better
than those of ANF. On the right, we plot the average relative error in
estimating traffic that belongs to two different applications - telnet and
Kazaa, using the two flow measurement solutions. While the accuracy of both the
estimates reduces as the attack rate increases, Flow Slices provides better
accuracy than ANF.
While these results do not prove that for all traffic mixes, Flow Slices perform better than other solutions, these results do show the efficacy of the Flow Slices on realistic traffic mixes. When we apply inactivity timeouts to the Flow Slices, it results in much better re-use of memory at the cost of a small loss in accuracy and a little increase in the total volume of flow records reported.