
2006 USENIX Annual Technical Conference Abstract
Pp. 261–266 of the Proceedings
Cutting through the Confusion: A Measurement Study of Homograph Attacks
Tobias Holgers, David E. Watson, and Steven D. Gribble, University of Washington
Abstract
Web homograph attacks have existed for some time, and the recent
adoption of International Domain Names (IDNs) support by browsers and
DNS registrars has exacerbated the problem [Gabr02]. Many
international letters have similar glyphs, such as the Cyrillic letter
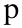 (lower case 'er,' Unicode 0x0440) and the Latin letter p.
Because of the large potential for misuse of IDNs, browser vendors,
policy advocates, and researchers have been exploring techniques for
mitigating homograph attacks [=Mozi05, Appl05, Oper05, Mark05]. (lower case 'er,' Unicode 0x0440) and the Latin letter p.
Because of the large potential for misuse of IDNs, browser vendors,
policy advocates, and researchers have been exploring techniques for
mitigating homograph attacks [=Mozi05, Appl05, Oper05, Mark05].
There has been plenty of attention on the problem recently, but we are
not aware of any data that quantifies the degree to which Web
homograph attacks are currently taking place. In this paper, we use a
combination of passive network tracing and active DNS probing to
measure several aspects of Web homographs. Our main findings are
four-fold.
First, many authoritative Web sites that users visit have several
confusable domain names registered. Popular Web sites are much more
likely to have such confusable domains registered.
Second, registered confusable domain names tend to consist of single
character substitutions from their authoritative domains, though
we saw instances of five-character substitutions. Most
confusables currently use Latin character homographs, but we
did find a non-trivial number of IDN homographs.
Third, Web sites associated with non-authoritative confusable domains
most commonly show users advertisements. Less common functions
include redirecting victims to competitor sites and spoofing the
content of authoritative site.
Fourth, during our nine-day trace, none of the 828 Web clients we
observed visited a non-authoritative confusable Web site.
Overall, our measurement results suggest that homograph attacks
currently are rare and not severe in nature. However,
given the recent increases in phishing incidents, homograph attacks
seem like an attractive future method for attackers to lure users to
spoofed sites.
- View the full text of this paper in HTML and PDF. Listen to the presentation in MP3 format.
 Until June 2007, you will need your USENIX membership identification in order to access the full papers. The Proceedings are published as a collective work, © 2006 by the USENIX Association. All Rights Reserved. Rights to individual papers remain with the author or the author's employer. Permission is granted for the noncommercial reproduction of the complete work for educational or research purposes. USENIX acknowledges all trademarks within this paper.
Until June 2007, you will need your USENIX membership identification in order to access the full papers. The Proceedings are published as a collective work, © 2006 by the USENIX Association. All Rights Reserved. Rights to individual papers remain with the author or the author's employer. Permission is granted for the noncommercial reproduction of the complete work for educational or research purposes. USENIX acknowledges all trademarks within this paper.
- If you need the latest Adobe Acrobat Reader, you can download it from Adobe's site.
|
