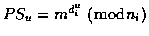
Next: mRSA Encryption.
Up: mRSA in detail
Previous: mRSA Key Setup.
A user generates a signature on a message
m as follows:
- 1. The user Ui first sends a hash of the message m to the
appropriate SEM.
- - SEM checks that Ui is not revoked and, if so, computes a
partial signature
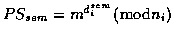 and replies with
it to the user. This PSsem is the token enabling signature generation.
and replies with
it to the user. This PSsem is the token enabling signature generation.
- - concurrently, Ui computes
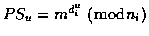
- 2. Ui receives PSsem and computes
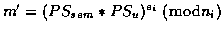 .
If m'=m, the signature is set to:
.
If m'=m, the signature is set to:
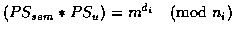 .
.
Note that in Step 2 the user Ui validates the response from the SEM.
Signature verification is identical to that in standard RSA.
Gene Tsudik
2001-05-10
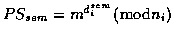 and replies with
it to the user. This PSsem is the token enabling signature generation.
and replies with
it to the user. This PSsem is the token enabling signature generation.