 |

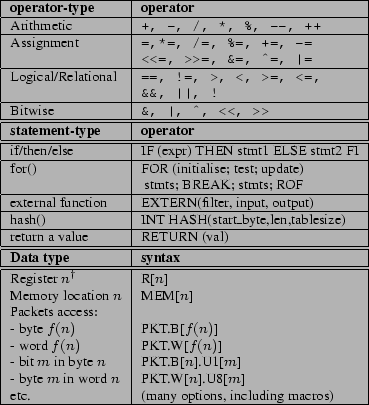
The FPL language is summarised in Figure 5. It supports
all common integer types (signed and unsigned bits, nibbles, octets,
words and double words) and allows expressions to get hold of any
field in the packet header or payload in a friendly manner. Moreover,
offsets in packets can be variable, i.e., determined by
an expression. For convenience, an extensible set of macros allows use
of shorthand for packet fields, e.g., instead of asking for bytes nine
and ten to obtain the IP header's protocol field, a user may abbreviate
to `IP_PROTO'. We briefly explain constructs that are not
intuitively clear.
FOR loop construct is limited to loops with a
pre-determined number of iterations.
The break instruction, allows one to exit the loop
`early'. In this case (and also when the loop finishes), execution
continues at the instruction following the ROF construct.
In FPL, an external function is called using the EXTERN
construct, where the parameters indicate the filter to call, the
offset in
![]() where the filter can find its input data (if any), and
the offset at which it should write its output, respectively. For
instance,
where the filter can find its input data (if any), and
the offset at which it should write its output, respectively. For
instance, EXTERN(foo,x,y) will call external function
foo, which will read its input from memory at offset ![]() , and
produce output, if any, at offset
, and
produce output, if any, at offset ![]() . Note that FFPF does not prevent
users from supplying bogus arguments. Protection comes from
authorisation control discussed in Section 3.4 and from
the compiler. The compiler checks the use of external functions in a
filter. An external function's definition prescribes the size of the
parameters, so whenever a user's filter tries to let the external
function read its input from an offset that would make it stray beyond
the bounds of the memory array, an error is generated. This is one of
the advantages of having a 'trusted' compiler (see also
Section 3.3.3. In addition, authorisation control can
be used to grant users access only to a set of registered functions.
. Note that FFPF does not prevent
users from supplying bogus arguments. Protection comes from
authorisation control discussed in Section 3.4 and from
the compiler. The compiler checks the use of external functions in a
filter. An external function's definition prescribes the size of the
parameters, so whenever a user's filter tries to let the external
function read its input from an offset that would make it stray beyond
the bounds of the memory array, an error is generated. This is one of
the advantages of having a 'trusted' compiler (see also
Section 3.3.3. In addition, authorisation control can
be used to grant users access only to a set of registered functions.
A small library of external filter functions has been implemented (including implementation of popular pattern matching algorithms, such as Aho-Corasick and Boyer-Moore). The implementation will be evaluated in Section 5. External functions in FPL can also be used to `script together' filters from different approaches (e.g., BPF+ [5], DPF [17], PathFinder [3], etc.), much like a shell script in UNIX.