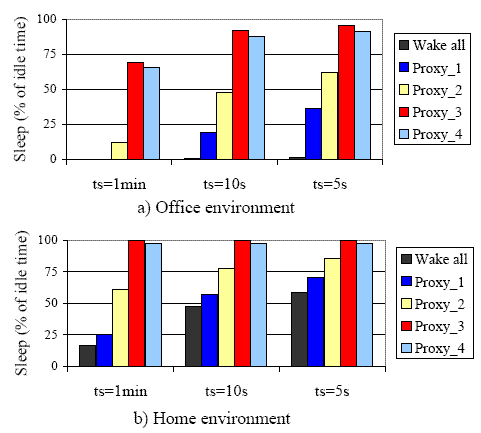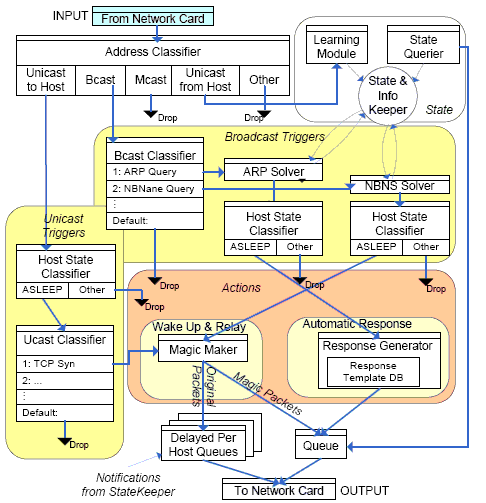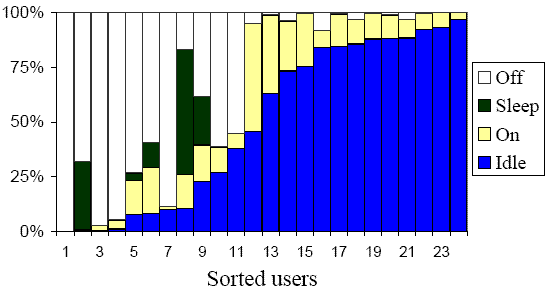

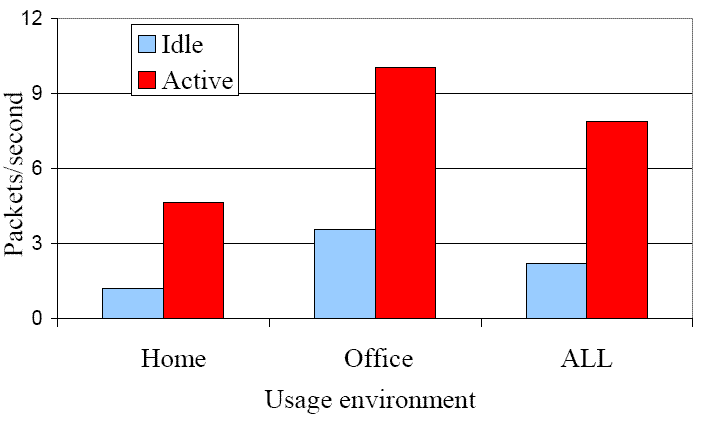
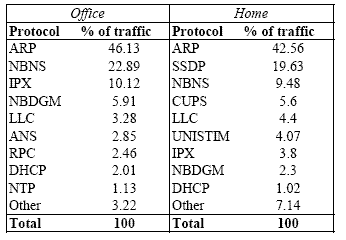
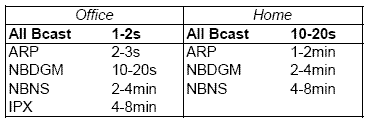
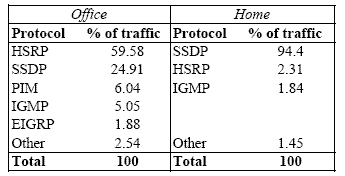
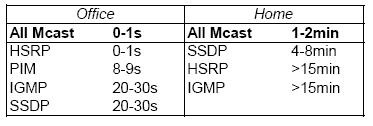
| Don't wake | HSRP, ARP, PIM, NBDGM, ICMP, IGMP, SSDP |
| Don't ignore | ARP (for me), NBNS, DHCP (for me) |
| Ignorable | HSRP, PIM, ARP (for others), IPX, LLC, EIGRP, DHCP | |
| Protocol | State | |
| ARP | IP address | |
| NBNS | NB names of machine and local services | |
| SSDP | Names of local plug-n-play services | |
| IGMP | Multicast groups the interface belongs to | |
| ICMP | IP address | |
| NBDGM | NB names of machine and local services. Ignores pkts. not destined to host, wakes host for rest | |