
TrInc: Small Trusted Hardware for Large Distributed Systems |
| Dave Levin | John R. Douceur | Jacob R. Lorch | Thomas Moscibroda |
| University of Maryland | Microsoft Research | Microsoft Research | Microsoft Research |
PeerReview [13] is a system that employs witnesses to collect a tamper-evident record of all messages in a distributed system for subsequent checking against a reference implementation. Unlike the remaining approaches we will discuss, PeerReview does not provide fault tolerance. Instead, it provides eventual fault detection and localization, which the system's designers argue leads to fault deterrence. The tamper-evident record is a distributed collection of logs that are authenticated using hash chains. The purpose of the tamper-evidence is to detect equivocation about the messages recorded in a log. As shown in Table 1, the communication required to collectively manage the tamper-evident message log is quadratic in the size of the witness set.
Accountability layer Trusted module Property PeerReview [13] Nysiad [14] A2M [7] TrInc No centralized trust ✓* ✓* Easy to deploy ✓ ✓ ✓ Easy to apply to existing protocols ✓ ✓† ✓‡ Immediate consistency ✓ ✓ ✓ No assumptions about protocol's determinism ✓† ✓ ✓ No additional online assumptions ✓ ✓ Additional communication overhead per protocol
message, with witness sets of size WO(W2) O(W2) O(1) O(1)
Table 1: Summary of the properties of various equivocation-fighting systems. *While PeerReview and Nysiad do not require centralized trust, they do make use of a PKI. †Nysiad deals with nondeterminism by treating nondeterministic events as inputs; this requires protocol changes for nondeterministic state machines. ‡We found that, although TrInc requires a protocol redesign, the modifications are often localized, and vastly simplify security procedures.
Global state:
Notation Meaning Kpriv Unique private key of this trinket Kpub Public key corresponding to Kpriv I ID of this trinket, the hash of Kpub A Attestation of this trinket's validity M Meta-counter: the number of counters this trinket has created so far Q Limited-size FIFO queue containing the most recent few counter attestations generated by this trinket
Per-counter state:
Notation Meaning i Identity of this counter, i.e., the value of M when it was created c Current value of the counter (starts at 0, monotonically non-decreasing) K Key to use for attestations, or 0 if Kpriv should be used instead
Figure 1: State of a trinket
Figure 2 shows the full API of a trinket, described in more detail in this subsection.
Function Operation Attest(i, c', h) Verifies that i is a valid counter with some value c and key K. Verifies that c ≤ c'. Creates an attestation a = ⟨ COUNTER, I, i, c, c', h⟩K; if K = 0, uses Kpriv instead of K. Adds a to Q. Sets c = c'. Returns a. GetCertificate() Returns a certificate of this trinket's validity: (I, Kpub, A). CheckAttestation(a, i) Returns a boolean indicating whether a is the output of invoking Attest on a trinket using the same symmetric key as the one associated with counter i. CreateCounter() Increments M. Creates a new counter with i = M, c=0, and K=0. Returns i. FreeCounter(i) If i is the identity of a valid counter, deletes that counter. ImportSymmetricKey( S, i) Verifies that S is an encrypted symmetric key decryptable with Kpriv. Decrypts it and installs the included key as K for counter i. GetRecentAttestations() Returns Q.
Figure 2: API of a trinket
- Assert that i is the identity of a valid counter.
- Let c be the value of that counter, and K be the key.
- Assert no roll-over: c ≤ c'.
- If K ≠ 0, then let a ← ⟨ I, i, c, c', h⟩K; otherwise let a ← ⟨ I, i, c, c', h⟩Kpriv.
- Insert a into Q, kicking out oldest value.
- Update c ← c'.
- Return a.
Algorithm 1: Attest(i, c', h, n)
Persistent Memory Asym. Crypto Symm. Crypto Fast Memory Bronze TrInc ✓ ✓ Silver TrInc ✓ ✓ ✓ Gold TrInc ✓ ✓ ✓ ✓
Table 2: Versions of TrInc with different performance.
Init()Append(queue q, value x)
- Create low and high counters:
Lq ← CreateCounter() ; Hq ← CreateCounter()- Return {Lq, Hq}
Lookup(queue q, sequence number n, nonce z)
- Bind h(x) to a unique counter (the current “high counter”):
a ← Attest(Hq.id, Hq.ctr+1, h(x))- Store the attestation in untrusted memory:
q.append(a, x)End(queue q, sequence number n, nonce z)
- If n < Lq, the entry was truncated. Attest to this by returning an attestation of the supplied nonce using the low-counter:
Attest(Lq.id, Lq.ctr, h(Forgotten || z))- If n > Hq, the query is too early. Attest to this by returning an attestation of the supplied nonce using the high-counter:
Attest(Hq.id, Hq.ctr, h(TooEarly || z))- Otherwise, return the entry in q that spans n, i.e., the one such that a.c < n ≤ a.c'. Note that if n < a.c', this means n was skipped by an Advance.
Truncate(queue q, sequence number n)
- Retrieve the latest entry from the given log:
{a,x} ← q.end()- Attest that this is the latest entry with a high-counter attestation of the supplied nonce:
a' ← Attest(Hq.id, Hq.ctr, z)- Return {a', {a,x}}
Advance(queue q, sequence number n, value x)
- Remove the entries from untrusted memory:
q.truncate(n)- Move up the low counter:
a ← Attest(Lq.id, n, Forgotten)
- Append a new item with sequence number n:
a ← Attest(Hq.id, n, h(x))- Store the attestation in untrusted memory:
q.append(a, x)Algorithm 2: Implementation of A2M with TrInc
Upon receipt of piece p:Upon sending piece p to neighbor j:
- Add p to bitfield B
- acurr ← Attest(i, |B|, h(p, B))
Periodically, for each neighbor j:
- Request an attestation from j with a random nonce.
- Do not send any piece other than p to j until j admits to having p.
Upon receiving an attestation request with nonce z:
- Request an attestation of j's current bitfield with a random nonce.
- atmp ← Attest(i, |B|, z).
- Reply with (acurr, atmp).
Algorithm 3: Fighting equivocation in BitTorrent
Secure DNS is intended to protect the integrity of the Internet domain name system. One identified threat [6] is that a resolving name server could be compromised and forge incorrect responses. The official solution to this threat is data origin identification in the DNS Security Extensions (DNSSEC), which uses public-key signatures to authenticate name updates. However, this solution does not address a threat in which the compromised name server replies to a query with out-of-date data, which would still bear a valid signature. Modifying DNSSEC with TrInc could address this problem by preventing the resolving name server from equivocating about whether it has received an update. Once it acknowledges receipt to the authoritative name server, it can no longer pretend it has not received the update.
Secure Origin BGP (soBGP) [44] is intended to protect the integrity of Internet routing updates. Like DNSSEC, soBGP uses public-key signatures to authenticate updates. Also like DNSSEC, soBGP is vulnerable to a threat in which a compromised router advertises out-of-date routes, which would still bear valid signatures. TrInc could address this problem by preventing a router from equivocating about whether it has received a routing update.
Distributed hash tables (DHTs), such as Chord [37], Bamboo [33], and Kademlia [27], are vulnerable to misbehaving nodes. In particular, a node can lie about which region of the keyspace it is responsible for. As nodes join and leave the DHT, these regions of responsibility change (sometimes quite rapidly [33]) in response to reconfiguration messages. A node can equivocate about whether it has received a particular message, which may allow it to claim responsibility for a region of the keyspace it does not own. TrInc could be used to prevent this equivocation.
Version control systems, such as CVS [41] and Subversion [29] are often run on remote servers. Thus, they are vulnerable to a threat model in which the server presents different views of the repository to different clients. Although this threat could be addressed at the block-store level [22], it might be more efficient to address it at the application level, in which case TrInc could prevent this equivocation.
Distributed auctions [42] are vulnerable to cheating participants. A bidder can try to manipulate others' bids by equivocating about the value of his current bid. An auctioneer can try to manipulate the bidding by equivocating about her reserve price for a particular auction. TrInc could protect against both of these classes of cheating, by preventing both bidders and auctioneers from equivocating.
Leader election protocols [25] rely on a quorum of participants to agree on a choice of leader. For a quorum of size q, it can legitimately happen that two groups of size q−1 will nominate different leaders. In this case, one participant can equivocate about which leader to nominate, causing the protocol to select two leaders concurrently. TrInc could be used to prevent this equivocation.
Digital signatures are used in many cryptographic protocols, but commonly use slow asymmetric key operations [17]. However, TrInc allows faster symmetric key operations to be used instead. To do so, a signer merely has to have his trinket attest to the hash of the message to be signed using a shared symmetric key. Since this attestation can only be generated by a party with access to the symmetric key, and since the hardware includes the ID in any attestation, no other party (except the trusted session administrator) can have generated the attestation. Thus, it functions effectively as a digital signature, verifiable by anyone whose trinket has the same symmetric key installed.
Operation Time (msec) Noop 6.14 ± 0.15 Attest (asymmetric, advance > 0) 230.24 ± 0.28 Attest (asymmetric, advance = 0) 198.21 ± 0.10 Attest (symmetric, advance > 0) 128.95 ± 0.08 Attest (symmetric, advance = 0) 105.90 ± 0.08 Verify Symmetric Attestation 85.81 ± 0.11
Table 3: TrInc microbenchmarks on a Gemalto .NET Smartcard, with 95% confidence intervals.
Time (msec) Operation TrInc A2M Noop 6.99 ± 0.01 Append 187.60 ± 0.15 551.93 ± 154 Lookup (Successful) 0.0122 ± 0.02 304.14 ± 6.87 Lookup (TooEarly) 162.24 ± 0.08 289.68 ± 2.23 Lookup (Forgotten) 162.35 ± 0.10 350.51 ± 1.43 End 162.31 ± 0.11 294.16 ± 2.04 Truncate 187.94 ± 0.10 28.99 ± 0.02 Advance 187.81 ± 0.12 288.20 ± 11.4
Table 4: TrInc-A2M microbenchmarks, with 95% confidence intervals.
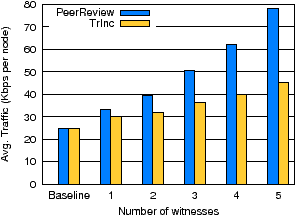
Figure 3: Reduction in PeerReview's message overhead due to TrInc.
Figure 4: Rate of progress for various BitTorrent clients when TrInc is used.
This document was translated from LATEX by HEVEA.