
Malicious end-hosts can create false positives by opening bogus TCP connections to keep a router from detecting that a particular route is stale or invalid. Adversaries noticing route advertisements from multiple vantage points (e.g., Routeviews [8]) can potentially notice mis-configurations before routers notice reachability problems. Such adversaries can exploit the situation and open bogus TCP connections.
We propose a combination of active dropping and retransmission checks as a countermeasure to reduce the probability of false positives.
Consider an adversary that has transmitted ![]() packets in a TCP
connection without receiving ACKs to retransmit a fraction,
packets in a TCP
connection without receiving ACKs to retransmit a fraction, ![]() , of
these packets. Let
, of
these packets. Let
![]() represent the
binomial coefficient for two values
represent the
binomial coefficient for two values ![]() and
and ![]() . The probability with
which the adversary is able to mislead the active dropping test is
given by
. The probability with
which the adversary is able to mislead the active dropping test is
given by
![]() . The probability with which the
retransmission check cannot detect an adversary is given by the tail
of the binomial distribution
. The probability with which the
retransmission check cannot detect an adversary is given by the tail
of the binomial distribution
![]() . Hence the overall probability,
. Hence the overall probability, ![]() , that our
algorithm does not detect an adversary is:
, that our
algorithm does not detect an adversary is:
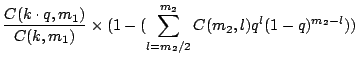
For a given prefix, the overhead of active dropping can be made very
small. By choosing ![]() and dropping only
and dropping only ![]() packets across
different TCP flows, we can reduce the probability of false positive,
packets across
different TCP flows, we can reduce the probability of false positive,
![]() , to be less than
, to be less than ![]() .
.
This countermeasure is applied only when we notice a discrepancy across different TCP connections to the same destination prefix, i.e., number of incomplete connections and complete connections are roughly the same. In this case, we sample and test whether a few complete connections are indeed bogus.