
Next: System Architecture
Up: Secure and Flexible Global
Previous: Other Protocols
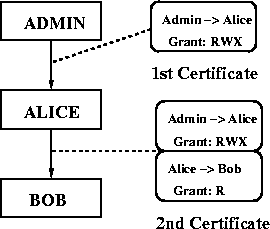
Figure 1:
Delegation of privileges, from the administrator to
Alice, and from Alice to Bob. The administrator grants Alice full
access by issuing her the first certificate. Alice can then delegate
read access to Bob by issuing him the second certificate. To be
granted access Bob must present a certificate chain consisting of
both certificates.
 |
Stefan Miltchev
4/8/2003


