
Next: Bcrypt Evaluation
Up: Bcrypt Algorithm
Previous: Bcrypt Algorithm
We have implemented bcrypt and deployed it as part of the
OpenBSD operating system. Bcrypt has been the default
password scheme since OpenBSD 2.1.
An important requirement of any bcrypt implementation is that
it exploit the full 128-bit salt space. OpenBSD generates the 128-bit
bcrypt salt from an arcfour (arc4random(3)) key
stream, seeded with random data the kernel collects from device
timings.
OpenBSD lets administrators select a password hashing scheme through a
special configuration file, passwd.conf(5).
passwd.conf allows detailed control over which type of
password to use for a given user or group. It also permits different
password schemes for local and YP passwords. For bcrypt, one
can also specify the cost. This lets people adjust password
verification time for increasing processor speed. At the time of
publication, the default cost is 6 for a normal user and 8 for the
superuser. Of course, whatever cost people choose should be
reevaluated from time to time.
To differentiate between passwords hashed by different algorithms,
every password function other than the original crypt prefixes its
output with a version identifier. Thus a single password file can
contain several types of password. In the current OpenBSD
implementation, bcrypt passwords start with ``$2a$'', while
MD5 crypt passwords with ``$1$.'' Because the result of
traditional crypt never begins with a ``$'', there is never any
ambiguity.
Table 1:
Time required to test a single password against a specified
password space when being able to perform 240,000 evaluations of
crypt per second. Password spaces above the separation can be
searched completely within 4 days. However this does not imply that
passwords chosen from below the separation are secure against password
guessing. These times are normal for traditional crypt nowadays.
| |
2c|10 |
2c|26 |
2c|36 |
2c|52 |
2c|62 |
2c|95 |
|
|
|
|
|
|
| 1|c||n |
2c|digits |
2c|lowercase |
2c|lowercase |
2c|mixed case |
2c|mixed case |
2c|keyboard |
|
|
|
|
|
|
| |
|
|
|
|
2c|alphanumeric |
|
|
2c|alphanumeric |
2c|characters |
|
|
|
| 4 |
0.04 |
sec |
1.9 |
sec |
7 |
sec |
30.5 |
sec |
61.6 |
sec |
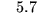 |
min |
| 5 |
0.4 |
sec |
49.5 |
sec |
4.2 |
min |
26.4 |
min |
1.1 |
hours |
9 |
hours |
| 6 |
4.2 |
sec |
21.5 |
min |
2.5 |
hours |
22.9 |
hours |
2.7 |
days |
35.5 |
days |
| 7 |
41.6 |
sec |
9.3 |
hours |
3.8 |
days |
49.6 |
days |
169 |
days |
9.2 |
years |
| 8 |
6.9 |
min |
10 |
days |
136 |
days |
7 |
years |
28.8 |
years |
875 |
years |
| 9 |
1.2 |
hours |
261 |
days |
13.4 |
years |
366 |
years |
1786 |
years |
83180 |
years |


Next: Bcrypt Evaluation
Up: Bcrypt Algorithm
Previous: Bcrypt Algorithm
Niels Provos and David Mazieres
4/28/1999
